
by Dan Humphries
Ransomware is a type of malware that encrypts the files on a computer, then charges the user a fee to regain access. New strains appear online with alarming frequency, and traditional anti-virus is powerless to prevent these attacks until they have been identified—leaving many businesses at risk.
In this report, we investigate the preparedness of decision-makers at small and midsize businesses (SMBs) to protect their companies against ransomware, and provide advice from cybersecurity experts on how to avoid disaster.
Key Findings:
- Sixty-seven percent of SMB decision-makers claim they would never pay a ransom to regain access to company files if their systems were infected with ransomware.
- However, only 23 percent of SMBs in our sample say they are “very confident” their data is secure from a ransomware attack.
- Thirty-one percent of SMBs have erratic or non-existent file backups—meaning they would have to either pay the ransom in the event of an attack, or lose the files.
- Only 34 percent of SMBs test their file backups regularly to ensure that data has been properly saved and is retrievable.
- Almost one-quarter (23 percent) of SMBs say they do not currently have a recovery plan for restoring backed-up data.
Introduction
Cybercriminals are relentless. As security tools become more sophisticated, crooks devise ever more devilish ways of stealing from their targets. New threats appear and old ones return, albeit in more virulent forms.
Such is the case with ransomware: In its original incarnation, unsuspecting victims would switch on their computers and see a message explaining they had been locked out of their system, and would need to pay the hacker a ransom to regain access. However, a simple computer reboot would usually let them back in.
Ransomware 2.0, on the other hand, actually does what it claims to—and the results can be catastrophic for businesses.
In late 2013, the ransomware CryptoLocker began to wreak havoc around the globe. The principle was simple: An attack might begin with a simple phishing email. One click and CryptoLocker would get to work, encrypting all personal files on the clicker’s computer—then searching for files to encrypt on other machines on the network.
Victims would see a screen instructing them to pay the hijackers a fee (usually $300, €300 euros or its equivalent in bitcoin) for the encryption keys, which would allow them to regain access. Along with the demand came a warning that if they did not pay within 72 hours, the encryption keys would be destroyed and the files lost forever.
By the time the screen appeared, it was too late to do anything about it. Even if CryptoLocker was removed, the files would remain encrypted. As Craig Williams, security outreach manager for tech giant Cisco, explains, well-funded criminal organizations employ skilled programmers to develop this type of malware.
“The reality is, the cryptography [is] done correctly. There’s really no way to crack it without getting the key,” Williams says.
CryptoLocker affected 500,000 victims before an international law enforcement operation shut down that particular scam. However, new forms of ransomware, such as CryptoWall and even a variant that targets PC game files, have since proliferated.
Indeed, Mark Parker, senior product manager at security firm iSheriff, says that at his company, “we have seen more than [one-quarter] of a million different ransomware variants [overall], and as many as 60,000 new variants in a single day.”
SMBs, which typically lack dedicated information technology departments and the resources to develop robust, multilayered defense posture, are particularly vulnerable. But are they prepared to defend against ransomware attacks? We surveyed business owners, executives and decision-makers to find out—then spoke to experts for advice on how to prevent facing the nasty choice between giving crooks cash or a catastrophic business shutdown.
The Majority of SMBs Are Unwilling to Pay Ransom
Our first question was simple: We asked respondents if, in the event their business computers were infected with ransomware that encrypted all of their files, they would pay a ransom to the hackers to regain access.
This begs the question: Is HR analytics software worth the investment? And if so, how does the use of analytics impact hiring and other key metrics?
Willingness to Pay Ransom in the Event of a Ransomware Attack
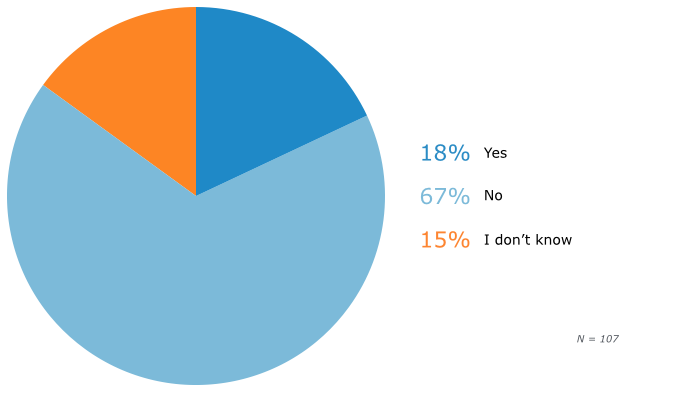
A solid 67 percent state that they would not negotiate with file hostage-takers. However, 18 percent—no doubt with limited technical skills, and skeptical of their ability to retrieve their business information any other way—say they would pay up. A further 15 percent “don’t know,” which similarly suggests a lack of confidence in the strength of their company’s defenses.
So which set of respondents is being more realistic? It is not unreasonable to assume that, forced to choose between extinction and handing a crook some cash to get the source of their livelihood back, many SMBs might opt to pay up. Indeed, in several cases (and to considerable media hooplah,) even law enforcement departments have capitulated and paid the ransom.
And yet, says Williams, paying the ransom is never a good idea.
Aside from the fact that it feeds the criminal machine, he says, “you have no assurances the malware was, in fact, removed. You could come back the next day and find a different piece of malware; they could re-encrypt your files again.”
Ultimately, the question of whether or not to pay will be decided by how well-prepared businesses are for this kind of attack—which is precisely what we investigated next.
Just 23 Percent ‘Very Confident’ Their Files Are Safe From Ransomware
Given the defiance SMB owners and operators expressed in response to our first question, we wanted to see if this attitude was backed up by a similarly robust confidence in the security of their company’s systems.
Confidence in Systems’ Protection From Ransomware
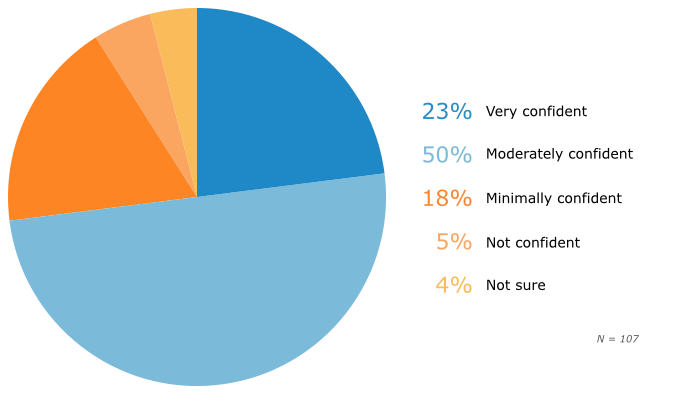
Here the picture is less bullish: only 23 percent are “very confident” they are prepared to handle a ransomware attack. Thus, many respondents in the first question are making a principled stand on ground that even they admit is rather shaky.
In fact, criminals keep waging ransomware attacks because they are so successful. Traditional anti-virus will only protect against previously identified strains—and even then, only if the anti-virus is regularly updated.
Still, the scenario is not hopeless. iSheriff’s Parker offers a few tips for keeping company systems safe:
- Do not open attachments from unknown senders;
- Ensure backups are recent and up-to-date;
- Do not click on links that seem suspicious;
- Do not allow any software of unknown origin to be installed on your system; and,
- Keep endpoint security up-to-date.
If a computer still manages to become infected, the user should remove it from the network immediately to prevent the malware from causing further damage.
The sad fact is that employees can, and will, click on dubious links, open attachments and install mysterious software. And even updated endpoint security tools could miss a new strain of ransomware if it is one that has never been seen before.
In these scenarios, Parker’s second piece of advice is essential. With recent and up-to-date backups in place, even if an employee (or executive) clicks on, for example, a fake LinkedIn invitation and accidentally encrypts every essential file on the network, it is possible to restore earlier file versions—and thus prevent business armageddon.
Nearly One-Third of SMBs Rarely or Never Back Up Company Files
This leads us to our next question: Are SMBs backing up the files on company computers and servers? Of course, backups are essential not only as a protection against ransomware, but as insurance against any situation that could cause the loss of vital business information. So, we asked respondents if they have a set schedule in place for doing so.
File Backup Protocol
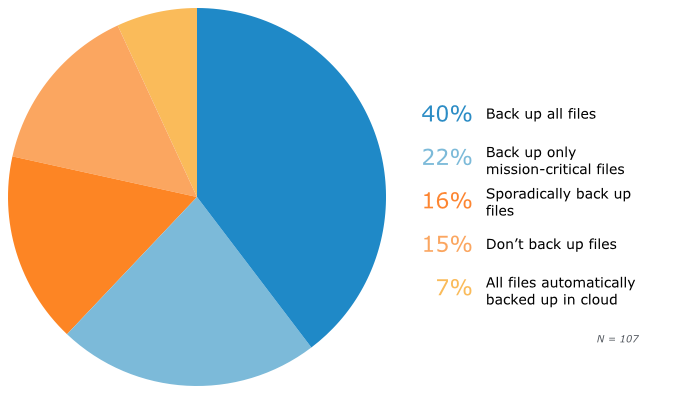
The good news is that 40 percent of respondents say they back up everything, while 22 percent take a more targeted approach, focusing on “mission-critical” files only. Seven percent exclusively use cloud-based office applications, such as Google Drive. While such applications are not entirely immune to ransomware, they do keep a record of changes made to documents, and allow users to return to earlier, unaffected versions.
And then there are the unprepared, of whom almost one-third have non-existent (15 percent) or completely erratic (16 percent) file-backup schedules. A solid 31 percent of respondents, combined, would thus be faced with the choice between file annihilation and paying off the crooks.
Cybersecurity expert Raj Goel recommends that businesses “implement full systems imaging backups”—a systems image being an exact copy of a drive. Goel says he backs up his clients’ systems at least twice a day, and in some cases, every four hours.
Greg Kelley, of computer forensics and discovery firm Vestige Digital Investigations, recommends backing up important documents, if not necessarily the whole drive.
“Keep seven to 14 days of backups, so that if the infection starts and it takes a few days to find, you are safe by going to older backups,” he says.
Of course, the more recent your backups, the quicker you will be able to return to business as usual. And this applies to any situation where a business needs to regain access to critical information—not just to ransomware attacks.
Only 34 Percent of SMBs Test Backups ‘Regularly’
While backing up files is a good start, even those who take such precautions may face an unpleasant discovery when they try to restore these files. Technology can (and does) go wrong, and many of us have experienced the deeply unpleasant sensation of discovering that something we thought we had saved is in fact nowhere to be found. It is not enough to just back up files; testing those backups is essential.
Frequency of File Backup Testing
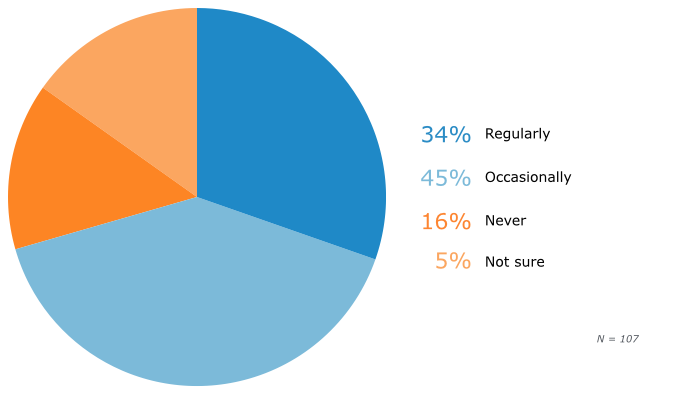
Here the results are more alarming, with only 34 percent of respondents saying that they test backups “regularly” to make sure the information they think they’re saving is actually retrievable. Almost half (45 percent) only test their backups “occasionally”—and it is all downhill from there.
So how often should a business test its backups? At a bare minimum, Goel recommends weekly testing of random files. It is essential to regularly verify that your files are both there and up-to-date: the older the files a business has to revert to, the more data that will be lost, and the greater the inconvenience of restoring them will be.
Indeed, security expert Rick Doten points out that unexpected problems can thwart even the best backups at the highest level. He recalls the story of a “large bank” that stored nightly backups on tape on its campus, but had not figured the local climate into its calculations. When the temperature caused a server to crash, the bank retrieved the tapes from the last backup.
However, “when attempting to put them in the tape reader, they didn’t fit, because the drive across campus in a hot box warped the tapes. So, even though the data was probably on the tape, the tape couldn’t physically be inserted,” Doten says.
While most SMBs are probably not using tape for their backups, no business should assume it is exempt from Murphy’s law: “Anything that can go wrong, will go wrong.”
Almost One-Quarter of SMBs Do Not Have a File-Recovery Plan
Finally, while an SMB may have solid backups in place, and may even have confirmed that the data is backed up and accessible, what happens if a ransomware attack still gets through? Will business owners be able to access that data quickly? After all, if it takes too long to restore backup files, a business can potentially lose more money than the price of a ransom.
Prevalence of File-Recovery Plans
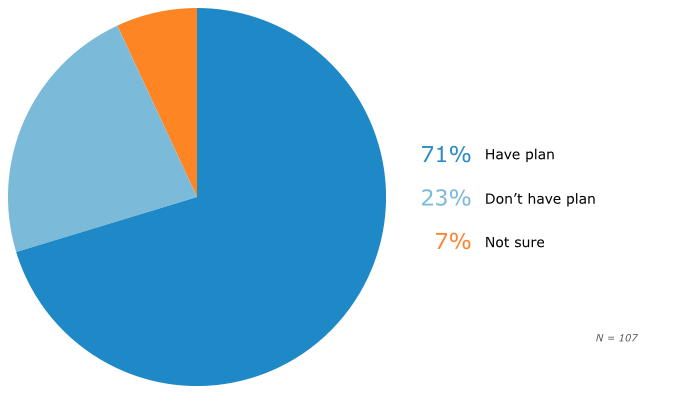
Among our respondents, 71 percent claim their company has a plan for restoring critical business information. Meanwhile, nearly one-third admit that it either does not (23 percent), or they are unsure whether their company has one (7 percent)—in which case it is unlikely their plan is any good, even if it does exist.
Meanwhile, since only 34 percent of respondents (in the previous section) regularly test their file backups to ensure the data is there, it seems likely that many of these plans are purely theoretical, and would fail if a crisis struck.
Rich Silva is the founder and president of managed IT service firm Pain Point IT Solutions. He says that a sound recovery solution should involve a combination of both backups to a local network device and backups to the cloud. Having only cloud or only off-site backup is not a sound recovery solution, he explains, as it can take too long to restore files.
“For example, it would take approximately 48 minutes to send 250 GB of data on a wired gigabit network, whereas it would take approximately 18 hours and 57 minutes for the same 250 GB of data to come down the pipe over the Internet,” Silva says.
To avoid disaster, SMB decision-makers should thus make sure they are not only saving their company data, but that they can quickly access that data in an emergency.
Conclusions
As our data shows, many SMBs are unprepared for a ransomware attack.
In the words of one expert:
There are no known working remedies, but if you plan for [a ransomware attack], it’s as annoying as the cold or flu: a minor hit in productivity, but survivable. If you don’t plan for it, it’ll hit like ebola: Infection recovery will be expensive, and may be incurable. Raj Goel, cybersecurity expert
Simple preparations that can reduce the risk to SMBs include training employees to recognize phishing attacks and teaching them not to click on suspicious links or to download attachments from an unknown source. Backing up and testing company files and keeping anti-malware up-to-date are also effective preventative measures.
Sound preparations will also benefit the wider community. The harder it becomes for criminals to deploy ransomware attacks, the sooner they will stop infecting computers with them. Of course, this does not mean they will have some transcendent conversion experience, hang up their black hats and resolve to make money honestly. Instead, they will develop new threats and try again. But why make life easier for them in the meantime?
Methodology
To collect the data in this report, we conducted an online, mobile survey of 107 owners and decision-makers at U.S. businesses with fewer than 1000 employees. We asked six questions, and collected 107 responses per question. All survey questionnaires undergo an internal peer review process to ensure clarity in wording.
Sources attributed and products referenced in this article may or may not represent partner vendors of Software Advice, but vendor status is never used as a basis for selection. Interview sources are chosen for their expertise on the subject matter, and software choices are selected based on popularity and relevance.
Expert commentary solely represents the views of the individual. Chart values are rounded to the nearest whole number.
Source: http://www.softwareadvice.com/security/industryview/ransomware-smb-report-2015/
